Investigation #2: Ensuring compliance with security regulations and catching leaked data
In an audit, examiners look for evidence of compliance with security regulations. Many enterprise IT teams now use network forensics to ensure that traffic complies with regulations and to demonstrate that compliance to auditors.
Using tools like the Peer Map shown in the previous section, IT engineers can monitor and record traffic patterns, demonstrating to auditors which users have access to which resources, and which devices are talking to which other devices.
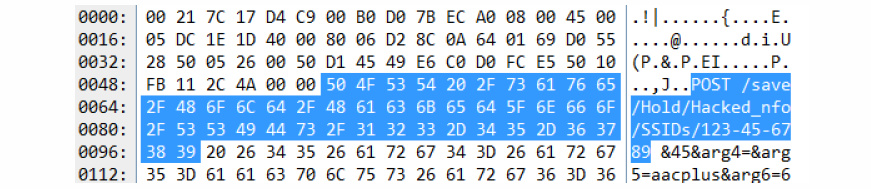
They can also configure filters based on regular expressions (Regex expressions) to look for traffic that may include personal information. The filters they use look for any packet that appears to include any number that seems like an SSID, a phone number, credit card numbers (strings of 16 digits), etc., that are sent in clear text. Since these filters only look for the specific packets with the personal data, they expect to never capture a packet. If the filters do find matches, the network forensics solution alerts the IT team through syslog and SNMP traps, so IT engineers can review the data immediately to prevent additional loss of data. An example of an advanced pattern filter in Omnipeek that filters the POST operation for specific traffic is shown below.
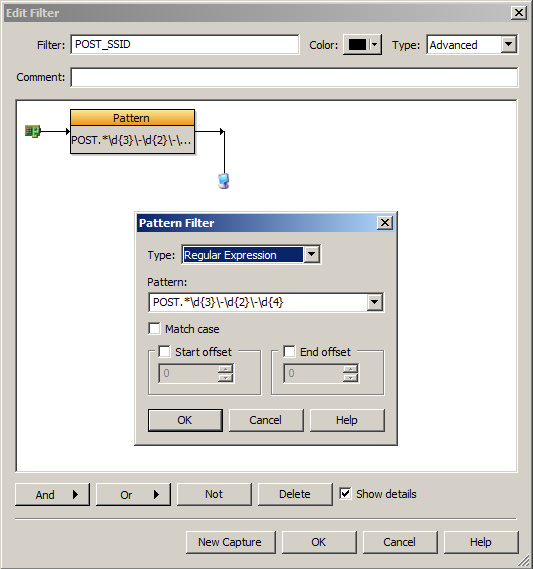
Packet-level capture enables IT engineers and security experts to examine decoded traffic and discover exactly how a security breach is occurring. The screenshot below shows packet decodes from traffic that includes an HTTP POST command containing data that seems to include hacked Social Security IDs.
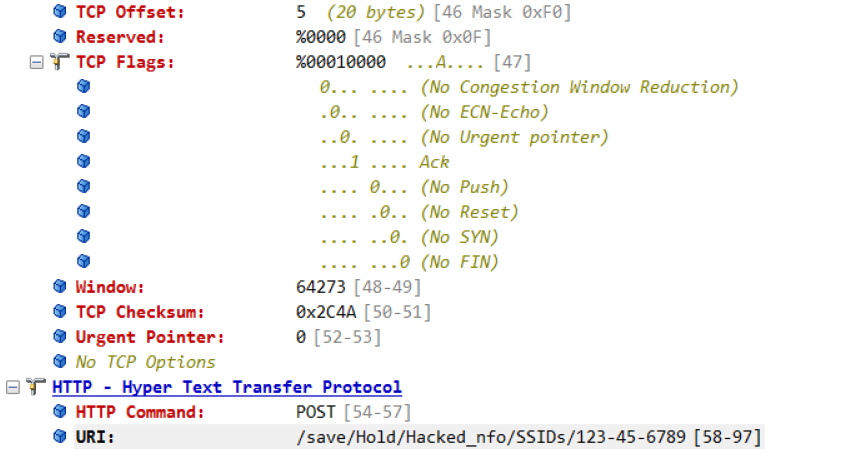
The hex decode below shows another view of this problematic traffic, including the suspicious POST operation.